Supply Chain Attack: Difference between revisions
Appearance
Created page with "FIle:Fig1-Solorigate-attack-chain.png|650px|right|Solorigate malware infection chain ([https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromise..." |
No edit summary |
||
| Line 1: | Line 1: | ||
[[FIle:Fig1-Solorigate-attack-chain.png|650px|right|Solorigate malware infection chain ([https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/ Flowchart from Microsoft Security blog])]] A '''Supply Chain Attack''' is when a threat actor makes use of unsecured network protocols, unprotected server infrastructures, or unsafe coding practices. The supply chain attacker breaks in, changes source codes, and hides malware in build and update processes.<ref>[https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/supply-chain-malware Supply Chain Malware, Microsoft]</ref> | [[FIle:Fig1-Solorigate-attack-chain.png|650px|right|thumbnail|Solorigate malware infection chain ([https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/ Flowchart from Microsoft Security blog])]] A '''Supply Chain Attack''' is when a threat actor makes use of unsecured network protocols, unprotected server infrastructures, or unsafe coding practices. The supply chain attacker breaks in, changes source codes, and hides malware in build and update processes.<ref>[https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/supply-chain-malware Supply Chain Malware, Microsoft]</ref> | ||
==References== | ==References== | ||
Revision as of 19:23, 23 July 2021
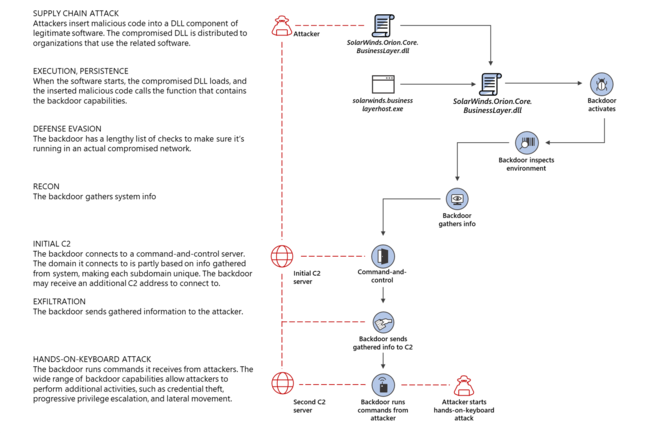
A Supply Chain Attack is when a threat actor makes use of unsecured network protocols, unprotected server infrastructures, or unsafe coding practices. The supply chain attacker breaks in, changes source codes, and hides malware in build and update processes.[1]
