National Institute of Standards and Technology: Difference between revisions
| Line 39: | Line 39: | ||
Profiles refer to the alignment between each organization's requirements and objectives, risk appetite, and resources and the desired outcomes of the Framework. The profile system is meant to help organizations identify opportunities for improving their cybersecurity posture by comparing their current profiles with their target profiles. | Profiles refer to the alignment between each organization's requirements and objectives, risk appetite, and resources and the desired outcomes of the Framework. The profile system is meant to help organizations identify opportunities for improving their cybersecurity posture by comparing their current profiles with their target profiles. | ||
===C3=== | |||
The Department of Homeland Security's Critical Infrastructure Cyber Community (C3) Voluntary Program helps owners and operators align their organizations with the framework and manage their cyber risks. | The Department of Homeland Security's Critical Infrastructure Cyber Community (C3) Voluntary Program helps owners and operators align their organizations with the framework and manage their cyber risks. | ||
Revision as of 18:16, 19 July 2021
| Industry: | Government |
| Founded: | 1901 |
| Headquarters: | Gaithersburg, Maryland |
| Country: | USA |
| Employees: | Approximately 3,400 (2021) |
| Website: | https://www.nist.gov/ |
The National Institute of Standards and Technology (NIST) is a physical sciences laboratory and non-regulatory agency. As part of the United States Department of Commerce, its mission is to promote American innovation and industrial competitiveness. NIST's laboratory programs include nanotechnology, engineering, information technology, neutron research, material measurement, and physical measurement. The institute was founded on March 3, 1901, as the National Bureau of Standards, and it became NIST in 1988.[1]
Cybersecurity Framework[edit | edit source]
Version 1.0[edit | edit source]
History[edit | edit source]
In February 2013, recognizing the national and economic security of the United States depends on the reliable function of critical infrastructure, President Barak Obama issued Executive Order 13636, "Improving Critical Infrastructure Cybersecurity," ordering NIST to work with stakeholders to develop a voluntary framework based on existing standards, guidelines, and practices for reducing cyber-risks to Critical Infrastructure. On December 18, 2014, the Cybersecurity Enhancement Act of 2014 (CEA) authorized the Department of Commerce, through NIST, to develop voluntary standards to reduce cyber-risks to critical infrastructure.[2] The law also ordered the Office of Science and Technology Policy to develop a federal cybersecurity research and development plan. Section 502 required the Director of NIST to ensure interagency coordination toward the development of international technical standards for IT security and transmit to Congress a plan.
Framework Development[edit | edit source]
February 26, 2013: RFI to Develop a Framework to Improve Critical Infrastructure Cybersecurity - February 12, 2014: Framework 1.0 Publication.
- One year after the release of Executive Order 13636 and following one RFI, five workshops, and one RFC, NIST released version 1.0 of the Framework for Improving Critical Infrastructure Cybersecurity.[3]
Components[edit | edit source]
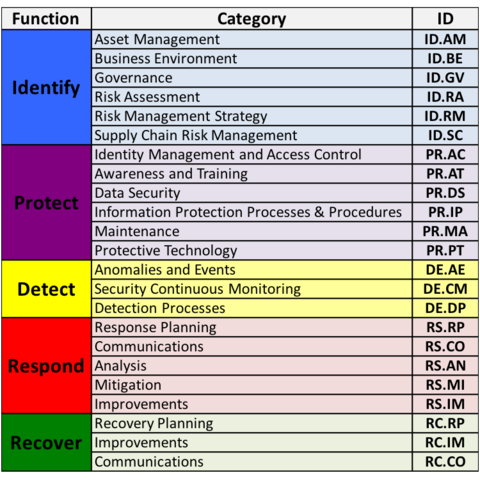
The resulting Cybersecurity Framework consists of voluntary standards, guidelines, and practices for promoting critical infrastructure protection. The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles.[4]
Core[edit | edit source]
The core is a set of desired cybersecurity activities and outcomes organized into Categories and aligned to Informative References.
Tiers[edit | edit source]
The tiers do not describe maturity levels; rather, they describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the Framework. It is up to each organization to decide its target tier. The Tiers range from "partial" to "adaptive," reflecting an increasing degree of rigor, integration among cybersecurity risk decisions, and information sharing between the organization and external parties.[5]
Profiles[edit | edit source]
Profiles refer to the alignment between each organization's requirements and objectives, risk appetite, and resources and the desired outcomes of the Framework. The profile system is meant to help organizations identify opportunities for improving their cybersecurity posture by comparing their current profiles with their target profiles.
C3[edit | edit source]
The Department of Homeland Security's Critical Infrastructure Cyber Community (C3) Voluntary Program helps owners and operators align their organizations with the framework and manage their cyber risks.

