General Data Protection Regulation
The Global Data Protection Regulation (GDPR) or Regulation (EU) 2016/679[1] is a regulation aimed at protecting all EU citizens and residents from privacy and data breaches. It was adopted on 14 April 2016 by the European Parliament (EP) after four years of collaborative drafting and negotiations.[2] The regulation is also an update of Data Protection Directive. Enforcement for the GDPR goes into effect on 25 May 2018.[3]
The GDPR places specific legal obligations on 'controllers' and 'processors', those who acts as intermediaries between the user/consumer and themselves, the government or any other actor. The controller determines how and why data is processed and processors act on the controller's behalf. Processors maintain data records and are held responsible in case of a breach.
With the update on existing legislation, the GDPR is more precise and inclusive of what constitutes private information than its predecessor. Personal data, that is anything that can identify a user, including an IP address is included, as well as 'sensitive personal data' which may include genetic and biomedical data.
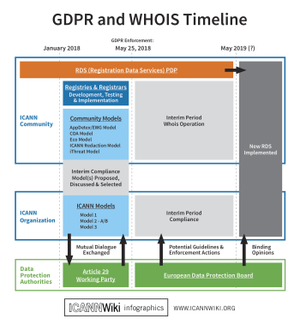
GDPR and WHOIS edit
The GDPR directly impacts the domain name space, most notability the WHOIS service. Prior to the GDPR enforcement date, ICANN's contracted parties (Registries and Registrars) expressed concern about their about to comply with their contractual requirement and be GDPR compliant. In light of this concern and the uncertainty around the implications of GDPR on WHOIS, ICANN announced that it would defer action against registries and registrars for noncompliance related to registration data.[4]
Information Security edit
Information security continues to shift left, whether that be with known secure starting templates or more frequent code scanning via up-to-date cloud services and continuous security testing, and SecOps will play a crucial role in helping to ensure improved security without compromising agility. Cognitive-enabled tools will again be key to faster identification and resolution.
The availability of new hosting technologies such as Kubernetes by the large cloud infrastructure-as-a-service (IaaS) providers will bring interesting new challenges. Adopters must look beyond the hype when selecting vendors and consider key security considerations, including:
Network protection. Are sufficient firewall capabilities provided by the service provider Hosting infrastructure security. Is the responsibility shared, and how does it impact our service availability
References edit
- ↑ Regulation (EU) 2016/679 of the European Parliament and of the Council 27 April 2016
- ↑ Lexology - EU General Data Protection Regulation Finally Adopted 15 April 2016
- ↑ Reform of EU data protection rules. Retrieved 27 Jun 2017.
- ↑ ICANN Contractual Compliance Statement Accessed 2 February 2018