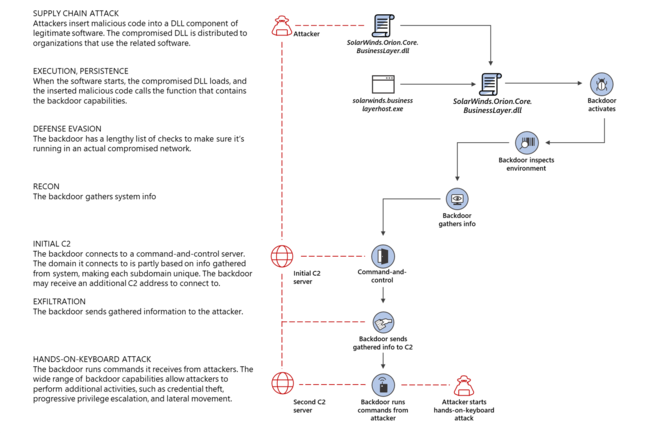
Supply Chain Attack
A Supply Chain Attack is when a threat actor makes use of unsecured network protocols, unprotected server infrastructures, or unsafe coding practices. The supply chain attacker breaks in, changes source codes, and hides malware in build and update processes.[1]