MITRE ATT&CK: Difference between revisions
No edit summary |
m added Category:DNS Abuse Responses using HotCat |
||
| (15 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
'''MITRE ATT&CK''' is a free framework that outlines all of the possible approaches cyber threat actors make take. The knowledge base, which is based entirely on real-world observations, offers a foundation for the development of specific threat models and methodologies for private, government, and [[Cybersecurity]] sectors.<ref>[https://attack.mitre.org/ About MITRE Attack, MITRE]</ref> The framework has one component for enterprise IT networks and clouds, and another for mobile devices. | '''MITRE ATT&CK''' is a free framework that outlines all of the possible approaches cyber threat actors make take. The knowledge base, which is based entirely on real-world observations, offers a foundation for the development of specific threat models and methodologies for private, government, and [[Cybersecurity]] sectors.<ref>[https://attack.mitre.org/ About MITRE Attack, MITRE]</ref> The framework has one component for enterprise IT networks and clouds, and another for mobile devices. | ||
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. There are different matrices of cyberattack techniques, sorted by tactics, for Windows, Linux, Mac, and mobile systems. The teams that use the ATT&CK model can document and track what threat actors are doing at the various stages of a cyberattack to infiltrate the network and exfiltrate data.<ref>[https://www.varonis.com/blog/mitre-attck-framework-complete-guide/ ATT&CK Complete Guide, Varonis]</ref> | ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. There are different matrices of cyberattack techniques, sorted by tactics, for Windows, Linux, Mac, and mobile systems. The teams that use the ATT&CK model can document and track what threat actors are doing at the various stages of a cyberattack to infiltrate the network and exfiltrate data.<ref>[https://www.varonis.com/blog/mitre-attck-framework-complete-guide/ ATT&CK Complete Guide, Varonis]</ref> ATT&CK can be used to run an adversary emulation, which is the process of assessing the security of a technology domain by applying cyber threat intelligence about specific adversaries to verify an organization's capacity to detect and mitigate adversarial activity. It can also be used for red teaming, which is an exercise in completing a breach without being detected.<ref>[https://attack.mitre.org/docs/ATTACK_Design_and_Philosophy_March_2020.pdf ATT&CK Design and Philosophy, MITRE 2020]</ref> ATT&CK can be used to construct and test behavioral analytics; to assess tools, monitoring, and mitigations of existing defenses in order to prioritize investments in security improvement; to determine how effective a Security Operations Center is at detecting, analyzing, and responding to intrusions; and to understand and document threat group profiles behaviorally, agnostic of the tools the groups may use.<ref>[https://attack.mitre.org/docs/ATTACK_Design_and_Philosophy_March_2020.pdf ATT&CK Design and Philosophy, MITRE 2020, pgs 13-14]</ref> | ||
==History== | ==History== | ||
In 2013, the Mitre Corporation, an American nonprofit managing federally funded research and development centers, started ATT&CK to document common tactics, techniques, and procedures that [[Threat Actor#Types|Advanced Persistent Threat]]s (APTs) use against [[Microsoft|Windows]] networks. It began as a documentation research project called "FMX," which investigated endpoint telemetry data and analytics usage with the aim of improving post-compromise detection. ATT&CK became the basis for testing the efficacy of sensors and analytics and is now the common language of cybersecurity offense and defense teams.<ref>[https://attack.mitre.org/resources/faq/ FAQs, MITRE]</ref> <br/> | In 2011, Lockheed Martin pioneered the [[Cyber Kill Chain]] methodology. In 2013, the Mitre Corporation, an American nonprofit managing federally funded research and development centers, started ATT&CK to document common tactics, techniques, and procedures that [[Threat Actor#Types|Advanced Persistent Threat]]s (APTs) use against [[Microsoft|Windows]] networks. It began as a documentation research project called "FMX," which investigated endpoint telemetry data and analytics usage with the aim of improving post-compromise detection. MITRE studied adversary TTPs in depth and built out the framework for a broader public. ATT&CK became the basis for testing the efficacy of sensors and analytics and is now the common language of cybersecurity offense and defense teams.<ref>[https://attack.mitre.org/resources/faq/ FAQs, MITRE]</ref> <br/> By spring 2021, the initially released ATT&CK framework had undergone many changes and was in its ninth version. | ||
By spring 2021, the initially released ATT&CK framework had undergone many changes and was in its ninth version. | |||
==Overview== | ==Overview== | ||
[[File:Mitre-attack-vs-cyber-kill-chain.png|thumbnail|[https://www.varonis.com/blog/mitre-attck-framework-complete-guide/ ATT&CK vs. Kill Chain, Varonis]]]The framework | [[File:Mitre-attack-vs-cyber-kill-chain.png|thumbnail|[https://www.varonis.com/blog/mitre-attck-framework-complete-guide/ ATT&CK vs. Kill Chain, Varonis]]]The framework is a kind of periodic table that lists and organizes malicious actor behaviors.<ref>[https://attackiq.com/lp/mitre-attack-for-dummies/ MITRE ATT&CK for Dummies, AttackIQ]</ref> It offers a common vision of the threat landscape, covering four conceptual issues with the overarching aim of assisting proactive offense rather than reactive defense.<ref>[https://medium.com/mitre-attack/att-ck-101-17074d3bc62 ATT&CK 101, Medium]</ref> | ||
# '''Behaviors''': ATT&CK reflects patterns of use rather than indicators of activities, such as domains, [[IP address]]es, file hashes, registry keys, because threat actors can easily change the latter. They are useful for detection, but they don't holistically capture how threat actors interact with systems. | # '''Behaviors''': ATT&CK reflects patterns of use rather than indicators of activities, such as domains, [[IP address]]es, file hashes, registry keys, because threat actors can easily change the latter. They are useful for detection, but they don't holistically capture how threat actors interact with systems. | ||
# '''Models''': ATT&CK is meant to provide less high-level lifecycle and [[Cyber Kill Chain]] models because too much abstraction makes them unhelpful. | # '''Models''': ATT&CK is meant to provide less high-level lifecycle and [[Cyber Kill Chain]] models because too much abstraction makes them unhelpful. | ||
| Line 23: | Line 22: | ||
Procedures refer to the actual implementation of the techniques. | Procedures refer to the actual implementation of the techniques. | ||
[[File:ATT&CK_Enterprise_Matrix_Version_9_Overview.png|thumbnail|900px|Screenshot of [https://attack.mitre.org/matrices/enterprise/ MITRE ATT&CK Enterprise Matrix Version 9.0]]] | ==Enterprise== | ||
[[File:ATT&CK_Enterprise_Matrix_Version_9_Overview.png|thumbnail|900px|Screenshot of [https://attack.mitre.org/matrices/enterprise/ MITRE ATT&CK Enterprise Matrix Version 9.0]]] The project that led to the MITRE ATT&CK framework began with a focus on detecting enterprise network attacks. It was publicly released in May 2015 with 96 techniques organized under nine tactics. ATT&CK for Cloud was published in 2019 as part of Enterprise. The matrix is for Linux, macOS, Windows, AWS, Azure, GCP, SaaS, Office 365, and Azure AD. | |||
==ATT&CK Evaluations | ==ICS== | ||
In 2020, ATT&CK for Industrial Control Systems (ICS) was published, with a focus on adversaries with the goal of disrupting an industrial control process, destroying property or causing temporary or permanent harm or death to humans<ref>[https://collaborate.mitre.org/attackics/index.php/Overview#scite-f86e41ef0024879db61ed5701d27aafa Overview, ATT&CK for ICS]</ref> by attacking ICS generally found in sectors such as electric, water/wastewater, oil/natural gas, transportation, chemical, pharmaceutical, pulp and paper, food and beverage, and manufacturing.<ref>[https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-82r2.pdf SP 800-82, NIST]</ref> | |||
==Mobile== | |||
ATT&CK for Mobile was published in 2017 for the technology domains of Android and iOS. There is minimal overlap in the mitigation categories of Enterprise and Mobile.<ref>[https://attack.mitre.org/docs/ATTACK_Design_and_Philosophy_March_2020.pdf ATT&CK Design and Philosophy, MITRE 2020, pg 26]</ref> | |||
==ATT&CK Evaluations== | |||
MITRE Engenutiy (ME) provides vendors with assessments of their ability to defend against TTPs by emulating known behaviors and exercising common ATT&CK techniques, as well as push the market to more effectively secure the world’s networks. ME publishes the results to inform the community. The evaluations do not reflect competitive analysis; there are no scores, rankings, or ratings. However, they do compare how vendors approach threat detection.<ref>[https://mitre-engenuity.org/attackevaluations/ ATT&CK Evaluations, Mitre Engenuity]</ref> | MITRE Engenutiy (ME) provides vendors with assessments of their ability to defend against TTPs by emulating known behaviors and exercising common ATT&CK techniques, as well as push the market to more effectively secure the world’s networks. ME publishes the results to inform the community. The evaluations do not reflect competitive analysis; there are no scores, rankings, or ratings. However, they do compare how vendors approach threat detection.<ref>[https://mitre-engenuity.org/attackevaluations/ ATT&CK Evaluations, Mitre Engenuity]</ref> | ||
| Line 31: | Line 37: | ||
[[Category:Cybersecurity]] | [[Category:Cybersecurity]] | ||
[[Category:DNS Abuse Responses]] | |||
Latest revision as of 17:45, 29 October 2021
MITRE ATT&CK is a free framework that outlines all of the possible approaches cyber threat actors make take. The knowledge base, which is based entirely on real-world observations, offers a foundation for the development of specific threat models and methodologies for private, government, and Cybersecurity sectors.[1] The framework has one component for enterprise IT networks and clouds, and another for mobile devices. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. There are different matrices of cyberattack techniques, sorted by tactics, for Windows, Linux, Mac, and mobile systems. The teams that use the ATT&CK model can document and track what threat actors are doing at the various stages of a cyberattack to infiltrate the network and exfiltrate data.[2] ATT&CK can be used to run an adversary emulation, which is the process of assessing the security of a technology domain by applying cyber threat intelligence about specific adversaries to verify an organization's capacity to detect and mitigate adversarial activity. It can also be used for red teaming, which is an exercise in completing a breach without being detected.[3] ATT&CK can be used to construct and test behavioral analytics; to assess tools, monitoring, and mitigations of existing defenses in order to prioritize investments in security improvement; to determine how effective a Security Operations Center is at detecting, analyzing, and responding to intrusions; and to understand and document threat group profiles behaviorally, agnostic of the tools the groups may use.[4]
History
In 2011, Lockheed Martin pioneered the Cyber Kill Chain methodology. In 2013, the Mitre Corporation, an American nonprofit managing federally funded research and development centers, started ATT&CK to document common tactics, techniques, and procedures that Advanced Persistent Threats (APTs) use against Windows networks. It began as a documentation research project called "FMX," which investigated endpoint telemetry data and analytics usage with the aim of improving post-compromise detection. MITRE studied adversary TTPs in depth and built out the framework for a broader public. ATT&CK became the basis for testing the efficacy of sensors and analytics and is now the common language of cybersecurity offense and defense teams.[5]
By spring 2021, the initially released ATT&CK framework had undergone many changes and was in its ninth version.
Overview

The framework is a kind of periodic table that lists and organizes malicious actor behaviors.[6] It offers a common vision of the threat landscape, covering four conceptual issues with the overarching aim of assisting proactive offense rather than reactive defense.[7]
- Behaviors: ATT&CK reflects patterns of use rather than indicators of activities, such as domains, IP addresses, file hashes, registry keys, because threat actors can easily change the latter. They are useful for detection, but they don't holistically capture how threat actors interact with systems.
- Models: ATT&CK is meant to provide less high-level lifecycle and Cyber Kill Chain models because too much abstraction makes them unhelpful.
- Observation: ATT&CK relies on observed incidents so that the framework can be applied to real environments.
- Taxonomy: ATT&CK emphasizes generating and using common terminology across incidents for the sake of comparison, such as TTPs.
Terminology
Tactics
Tactics refer to the purpose behind an adversarial technique. It is the goal for performing the action, such as stealing credentials or gaining remote access.
Techniques
Techniques encompass the conceptual method for achieving the tactical goal in question.
Procedures
Procedures refer to the actual implementation of the techniques.
Enterprise
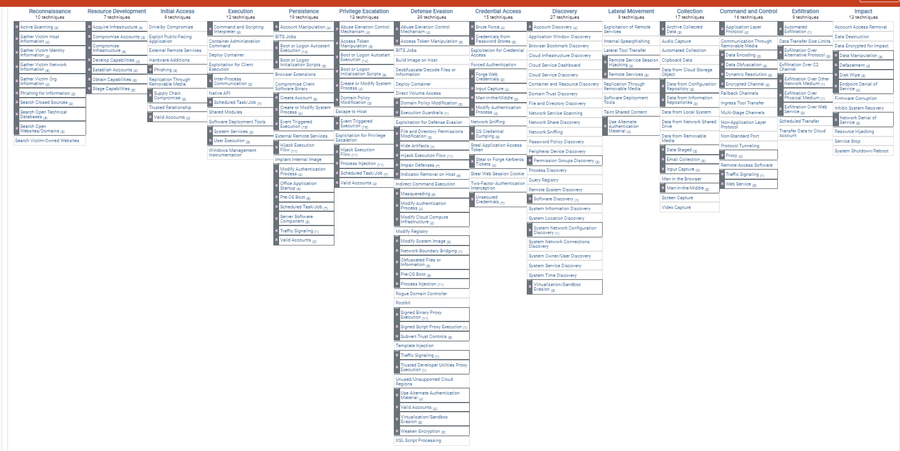
The project that led to the MITRE ATT&CK framework began with a focus on detecting enterprise network attacks. It was publicly released in May 2015 with 96 techniques organized under nine tactics. ATT&CK for Cloud was published in 2019 as part of Enterprise. The matrix is for Linux, macOS, Windows, AWS, Azure, GCP, SaaS, Office 365, and Azure AD.
ICS
In 2020, ATT&CK for Industrial Control Systems (ICS) was published, with a focus on adversaries with the goal of disrupting an industrial control process, destroying property or causing temporary or permanent harm or death to humans[8] by attacking ICS generally found in sectors such as electric, water/wastewater, oil/natural gas, transportation, chemical, pharmaceutical, pulp and paper, food and beverage, and manufacturing.[9]
Mobile
ATT&CK for Mobile was published in 2017 for the technology domains of Android and iOS. There is minimal overlap in the mitigation categories of Enterprise and Mobile.[10]
ATT&CK Evaluations
MITRE Engenutiy (ME) provides vendors with assessments of their ability to defend against TTPs by emulating known behaviors and exercising common ATT&CK techniques, as well as push the market to more effectively secure the world’s networks. ME publishes the results to inform the community. The evaluations do not reflect competitive analysis; there are no scores, rankings, or ratings. However, they do compare how vendors approach threat detection.[11]
References
- ↑ About MITRE Attack, MITRE
- ↑ ATT&CK Complete Guide, Varonis
- ↑ ATT&CK Design and Philosophy, MITRE 2020
- ↑ ATT&CK Design and Philosophy, MITRE 2020, pgs 13-14
- ↑ FAQs, MITRE
- ↑ MITRE ATT&CK for Dummies, AttackIQ
- ↑ ATT&CK 101, Medium
- ↑ Overview, ATT&CK for ICS
- ↑ SP 800-82, NIST
- ↑ ATT&CK Design and Philosophy, MITRE 2020, pg 26
- ↑ ATT&CK Evaluations, Mitre Engenuity
