MITRE ATT&CK: Difference between revisions
No edit summary |
|||
| Line 3: | Line 3: | ||
==History== | ==History== | ||
In 2013, the Mitre Corporation, an American nonprofit managing federally funded research and development centers, started ATT&CK to document common tactics, techniques, and procedures that [[Threat Actor#Types|Advanced Persistent Threat]]s ( | In 2013, the Mitre Corporation, an American nonprofit managing federally funded research and development centers, started ATT&CK to document common tactics, techniques, and procedures that [[Threat Actor#Types|Advanced Persistent Threat]]s (APTs) use against [[Microsoft|Windows]] networks. It began as a documentation research project called "FMX," which investigated endpoint telemetry data and analytics usage with the aim of improving post-compromise detection. ATT&CK became the basis for testing the efficacy of sensors and analytics and is now the common language of cybersecurity offense and defense teams.<ref>[https://attack.mitre.org/resources/faq/ FAQs, MITRE]</ref> <br/> | ||
By 2021, the initially released ATT&CK framework had undergone many changes and | By spring 2021, the initially released ATT&CK framework had undergone many changes and was in its ninth version. | ||
==Overview== | ==Overview== | ||
Revision as of 11:11, 30 July 2021
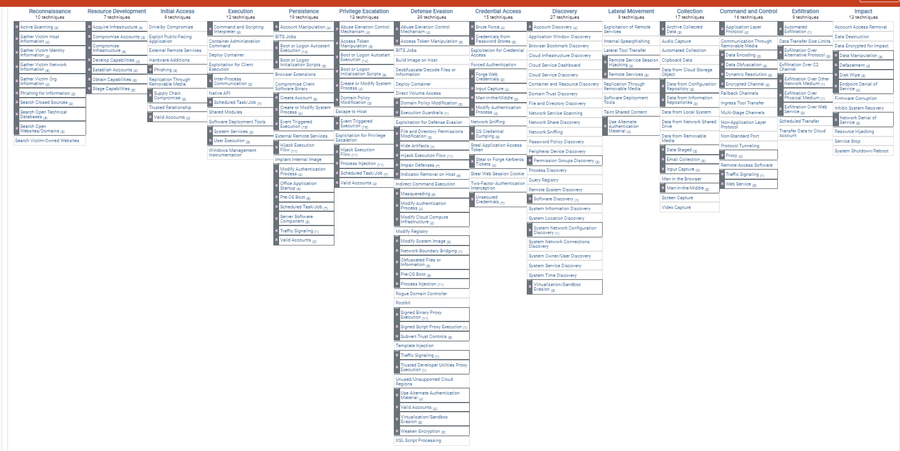
MITRE ATT&CK is a free framework that outlines all of the possible approaches cyber threat actors make take. The knowledge base, which is based entirely on real-world observations, offers a foundation for the development of specific threat models and methodologies for private, government, and Cybersecurity sectors.[1] The framework has one component for enterprise IT networks and clouds, and another for mobile devices. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. There are different matrices of cyberattack techniques, sorted by tactics, for Windows, Linux, Mac, and mobile systems. The teams that use the ATT&CK model can document and track what threat actors are doing at the various stages of a cyberattack to infiltrate the network and exfiltrate data.[2]
History
In 2013, the Mitre Corporation, an American nonprofit managing federally funded research and development centers, started ATT&CK to document common tactics, techniques, and procedures that Advanced Persistent Threats (APTs) use against Windows networks. It began as a documentation research project called "FMX," which investigated endpoint telemetry data and analytics usage with the aim of improving post-compromise detection. ATT&CK became the basis for testing the efficacy of sensors and analytics and is now the common language of cybersecurity offense and defense teams.[3]
By spring 2021, the initially released ATT&CK framework had undergone many changes and was in its ninth version.
Overview

The framework covers four conceptual issues with the overarching aim to assist proactive offense rather than reactive defense.[4]
- Behaviors: ATT&CK reflects patterns of use rather than indicators of activities, such as domains, IP addresses, file hashes, registry keys, because threat actors can easily change the latter. They are useful for detection, but they don't holistically capture how threat actors interact with systems.
- Models: ATT&CK is meant to provide less high-level lifecycle and Kill Chain models because too much abstraction makes them unhelpful.
- Observation: ATT&CK relies on observed incidents so that the framework can be applied to real environments.
- Taxonomy: ATT&CK emphasizes generating and using common terminology across incidents for the sake of comparison.
Terminology
Tactics
Tactics refer to the purpose behind an adversarial technique. It is the goal for performing the action, such as stealing credentials or gaining remote access.
Techniques
Techniques encompass the conceptual method for achieving the tactical goal in question.
Procedures
Procedures refer to the actual implementation of the techniques.