Ransomware: Difference between revisions
No edit summary |
m added Category:Featured using HotCat |
||
| (49 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
'''Ransomware''' | '''Ransomware''' | ||
is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. | is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. They threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid. | ||
==Darkside== | [[as-a-Service Model#Ransomware-as-a-Service|RaaS]] is a subscription for ransomware tools. RaaS allows cybercrime groups to extend their reach and decentralizes attacks, complicating efforts to disrupt them. The RaaS creators take a percentage of each successful ransom payment.<ref>[https://www.varonis.com/blog/ransomware-statistics-2021/ Ransomware Stats 2021, Varonis blog]</ref> | ||
==Recent Statistics and History-Making Events== | |||
:Average downtime due to ransomware: 21 days<ref>[https://www.coveware.com/blog/ransomware-marketplace-report-q4-2020C Ransomware Payments Fall as Fewer Companies Pay Data Exfiltration Extortion Demands, Feb 1, 2021]</ref><br/> | |||
:Average recovery time for organizations: 287 days<ref>[https://blog.emsisoft.com/en/37314/the-state-of-ransomware-in-the-us-report-and-statistics-2020/ The State of Ransomware in the US: Report and Statistics 2020, Emisoft Blog, Jan 18, 2021]</ref><br/> | |||
:Total victims paid to decrypt their data: US$350 million<ref>[https://blog.chainalysis.com/reports/ransomwareecosystem-crypto-crime-2021Chainalysis 2021 Crypto Crime Report]</ref><br/> | |||
:Change in payout from 2019 to 2020: 311% increase<ref>[https://blog.chainalysis.com/reports/ransomwareecosystem-crypto-crime-2021Chainalysis 2021 Crypto Crime Report]</ref><br/> | |||
:Total victims paid to decrypt their data: US$350 million<ref>[https://blog.chainalysis.com/reports/ransomwareecosystem-crypto-crime-2021Chainalysis 2021 Crypto Crime Report]</ref><br/> | |||
:Average individual payment: US$312,493<ref>[https://unit42.paloaltonetworks.com/ransomware-threat-assessments Ransomware Threat Assessments, Unit 42, Palo Alto Networks March 17, 2021]</ref><br/> | |||
:Year-over-year difference from 2019: 171% increase <ref>[https://unit42.paloaltonetworks.com/ransomware-threat-assessments Ransomware Threat Assessments, Unit 42, Palo Alto Networks March 17, 2021]</ref><br/> | |||
:Number of U.S.-based governments, healthcare facilities, and schools attacked: 2,400<ref>[https://securityandtechnology.org/wp-content/uploads/2021/04/IST-Ransomware-Task-Force-Report.pdf RTF Report 2021, pg. 7]</ref><br/> | |||
:The [[CISA|critical infrastructure sector]] that experienced more ransomware attacks than any other industry: Healthcare<ref>[https://purplesec.us/resources/cyber-security-statistics/#Healthcare%20Providers 2021 Cyber Security Stats, PurpleSec]</ref><br/> | |||
:On September 10, 2020, ransomware contributed to the first reported death related to a cyber attack, after an emergent patient had to be re-directed from a ransomware victim hospital in Germany.<ref>[https://www.zdnet.com/article/first-death-reported-following-a-ransomware-attack-on-a-german-hospital/ First Death from Ransomware, ZDNet]</ref> | |||
:On April 29, 2021, [[CISA|DHS Secretary Alejandro Mayorkas]] declared ransomware a national security threat.<ref>[https://breakingdefense.com/2021/04/ransomware-a-national-security-issue-new-report-argues-yes/ Breaking Defense]</ref> | |||
==Mitigation== | |||
* '''CISA''''s [https://www.cisa.gov/stopransomware#:~:text=Ransomware%20is%20a%20form%20of,ransom%20in%20exchange%20for%20decryption. StopRansomware.gov] recommends that individual users: | |||
# Update software and operating systems with the latest patches, because hackers most commonly attack outdated applications and operating systems; | |||
# Never click on links or open attachments in unsolicited emails; | |||
# Constantly back up data, keep it on a separate device, and store it offline; | |||
# Use strong passwords; and | |||
# Only connect to secure networks, use a VPN, and make sure you have a firewall.<ref>[https://us-cert.cisa.gov/ncas/tips/ST04-003 CISA Tips]</ref> | |||
: Recommendations for organizations include: | |||
# Heavily restrict user permissions to install and run software applications; | |||
# Enable the strongest spam filters possible; and | |||
# Configure firewalls to block access to known malicious [[IP Address]]es.<ref>[https://www.cisa.gov/stopransomware/ransomware-faqs Ransomware FAQs, CISA]</ref> | |||
* On April 29, 2021, the Institute for Security and Technology launched the [[Ransomware Task Force]] (RTF), which released a comprehensive framework outlining 48 actions and their timelines for governments and industry leaders to undertake to disrupt the ransomware business model and mitigate attacks' impacts.<ref>[https://securityandtechnology.org/ransomwaretaskforce/ RTF, IST]</ref> | |||
* Alternatives to payment include: | |||
:* working with the [[No More Ransom Project]], which helps victims decrypt data without paying attackers; | |||
:* working with law enforcement, such as the [[FBI]], immediately after noticing the attack | |||
* To manage the fallout, an industry has grown up around cyberattack recovery. Cyber insurance (aka [[cybersecurity]] insurance, cyber risk insurance, data breach insurance, or cyber liability insurance) protects against some of the financial and legal consequences of cyber risks and attacks. This industry is focused on mitigating the side effects of cyber attacks and data breaches.<ref>[https://www.zeguro.com/cyberinsurance Cyber insurance, Zeguro]</ref> The backstop support of insurance may encourage ransomware attackers, as insured victims may be more likely to pay.<ref>[https://www.propublica.org/article/the-extortion-economy-how-insurance-companies-are-fueling-a-rise-in-ransomware-attacks Extortion Economy, ProPublica]</ref> However, insurance providers generally require that clients adhere to baseline security practices, connect victims to recovery experts and law enforcement, and leverage market tools to incentivize security standards and discourage organizations from paying ransom.<ref>[https://securityandtechnology.org/wp-content/uploads/2021/04/IST-Ransomware-Task-Force-Report.pdf RTF Report, IST, pg 13]</ref> | |||
* [[Zero Trust]] architecture limits lateral movement and contains the blast radius or ransomware attacks.<ref>[https://venturebeat.com/2021/05/14/adopting-zero-trust-architecture-can-limit-ransomwares-damage/ Adopting zero trust architecture can limit ransomware’s damage, VentureBeat]</ref> | |||
==Debates== | |||
===To Pay or Not to Pay?=== | |||
''The "DON'T make it an option" Camp'' | |||
: On June 10, 2021, [[FBI]] Director [[Christopher Wray]] testified before Congress that companies should not pay the ransom because doing so encourages more of this kind of activity and that victims may pay the ransom but not get their systems back.<ref>[https://www.c-span.org/video/?512336-1/fbi-director-wray-testifies-oversight-bureau FIB Director testifies, CSPAN]</ref><br/> | |||
: U.S. Energy Secretary [[Jennifer Granholm]] supports legislation banning ransomware payments.<ref>[https://www.nbcnews.com/meet-the-press/video/granholm-i-would-support-law-banning-ransomware-payments-114399301786 Granholm on Meet the Press, NBC News]</ref> <br/> | |||
: The Biden administration formed a multi-agency task force working on freeze ransomware payments made through cryptocurrency platforms<ref>[https://www.cbsnews.com/news/ransomware-white-house-cybersecurity-task-force-calls-for-retaliation-russia/ White House Cybersecurity Task Force, CBS News]</ref> | |||
: New York introduced and North Carolina passed bills to prohibit municipal ransomware payments.<ref>[https://www.nysenate.gov/legislation/bills/2019/s7289 2019 NY Senate Bills]</ref><ref>[https://www.ncleg.gov/BillLookUp/2021/H813 2021 NC Senate Bills]</ref> | |||
''The "Maybe DO let it remain an option" Camp'' | |||
: [[Bryan Hornung]], the founder of cybersecurity firm [[Xact IT Solutions]], argued that if companies cannot pay ransoms, they will have to close their doors and lawsuits will proliferate; also, the attackers may seek to extort individuals whose data are compromised if organizations do not pay.<br/> | |||
: [[Ed Cabrera]], CCO at [[Trend Micro]], said that criminalizing ransom payments will lead hackers to make more lethal attacks and increase the pain.<ref>[https://www.forbes.com/sites/edwardsegal/2021/06/08/banning-ransomware-payments-could-create-new-crisis-situations/?sh=30ff48829828 Banning Ransomware payments could lead to new crises, Forbes]</ref><br/> | |||
: In the ''Harvard Business Review'', [[Rahul Telang]] opined that in attacking companies rather than consumers, ransomware is forcing organizations to pay a steep, direct price for lax security and ultimately focusing organizations' attention on improving their cybersecurity and protecting their networks.<ref>[https://hbr.org/2021/08/could-ransomware-attacks-ultimately-benefit-consumers Could Ransomware Attacks Ultimately Benefit Consumers? HBR, August 02, 2021 ]</ref> | |||
: [[Coveware]]'s core business model is negotiating ransomware sums.<ref>[https://www.coveware.com/blog/2021/7/23/q2-ransom-payment-amounts-decline-as-ransomware-becomes-a-national-security-priority Q2 Ransom Payments Decline, Coveware]</ref> | |||
==Notorious Cases== | |||
===Cobalt Strike=== | |||
Cobalt Strike is the legitimate, commercially available tool used by network penetration testers that has been co-opted by threat actors.<ref>[https://threatpost.com/cobalt-strike-cybercrooks/167368/ Cobalt Strike Usage Explodes Among Cybercrooks]</ref> It is also known as Agentemis, BEACON, and CobaltStrike, and the threat actors that have used it include APT 29, APT32, APT41, Anunak, Cobalt, Codoso, CopyKittens, DarkHydrus, FIN6, Leviathan, Mustang Panda, Shell Crew, Stone Panda, UNC1878, UNC2452, and Winnti Umbrella.<ref>[https://malpedia.caad.fkie.fraunhofer.de/details/win.cobalt_strike Cobalt Strike, Malpedia]</ref> | |||
===Maze Cartel=== | |||
[[File:Maze Cartel.png|500px|thumbnail|right|[https://analyst1.com/blog/ransom-mafia-analysis-of-the-worlds-first-ransomware-cartel Analyst1 Cartel Breadown]]] | |||
In June 2020, the Maze Cartel publically announced that TWISTED SPIDER, VIKING SPIDER, and LockBite were running a collaborative business arrangement.<ref>[https://www.crowdstrike.com/cybersecurity-101/ransomware/history-of-ransomware/ History of Ransomware, CrowdStrike]</ref> In November 2020, Twisted Spider announced they were shutting down the cartel operations.<ref>https://chaslescorp.com/the-rise-and-fall-of-maze-cartel/ The rise and fall of Maze Cartel, ChaslesCorp]</ref> | |||
The people who comprise the cartel originate from eastern Europe, primarily speak Russian, and ensure that their payloads do not execute on Russian victims. Twisted Spider used Maze ransomware from May 2019 to November 2020 and Egregor beginning in September 2020, each using its own malware, infrastructure, and online personas. The operators are very communicative with media, cybersecurity firms, and other cybercriminals.<ref>[https://analyst1.com/blog/ransom-mafia-analysis-of-the-worlds-first-ransomware-cartel Ransom Mafia, Analyst1]</ref> Viking Spider began its ransom operations in December 2019. Wizard Spider has multiple teams and has been participating in attacks since 2016. The Lockbit Gang was the first to automate attacks. SunCrypt was the first gang to introduce [[DoS Attack|denial of service attacks]] to extort victims.<ref>[https://analyst1.com/blog/ransom-mafia-analysis-of-the-worlds-first-ransomware-cartel Ransom Mafia, Analyst1]</ref> | |||
===Darkside=== | |||
Darkside is a group of hackers that carried out a significant ransomware attack in May 2021. | Darkside is a group of hackers that carried out a significant ransomware attack in May 2021. | ||
In August 2020, Darkside introduced its Ransomware-as-a-Service (RaaS) in a press release. The group provides web chat support to victims, builds intricate data leak storage systems with redundancy, and performs financial analysis of victims prior to attacking. The group is suspected to be former IT security professionals and is known to have a code of conduct that includes not attacking hospitals, schools, non-profits, or governments, but rather big organizations. After the May 2021 Colonial Pipeline attack, [[Varonis]]’s reverse engineering revealed that Darkside’s malware checked device language settings to ensure that they don’t attack Russia-based organizations.<ref>[https://www.varonis.com/blog/darkside-ransomware/ Analysis of Darkside, Varonis Blog]</ref> | In August 2020, Darkside introduced its Ransomware-as-a-Service (RaaS) in a press release. The group provides web chat support to victims, builds intricate data leak storage systems with redundancy, and performs financial analysis of victims prior to attacking. The group is suspected to be former IT security professionals and is known to have a code of conduct that includes not attacking hospitals, schools, non-profits, or governments, but rather big organizations. After the May 2021 Colonial Pipeline attack, [[Varonis]]’s reverse engineering revealed that Darkside’s malware checked device language settings to ensure that they don’t attack Russia-based organizations.<ref>[https://www.varonis.com/blog/darkside-ransomware/ Analysis of Darkside, Varonis Blog]</ref> | ||
Darkside has Windows and Linux toolsets | Darkside has Windows and Linux toolsets and is similar to NetWalker and REvil in that it has an affiliate program that offers anyone who helps spread their malware 10-25% of the payout. | ||
Darkside | Darkside | ||
*runs command and control over [[TOR]], | *runs [[Command and Control|command and control]] over [[TOR]], | ||
*avoids nodes where [[EDR]] is running, | *avoids nodes where [[EDR]] is running, | ||
*uses waiting periods, | *uses waiting periods, | ||
| Line 16: | Line 77: | ||
*performs anti-forensics techniques, such as deleting log files. | *performs anti-forensics techniques, such as deleting log files. | ||
==TrickBot== | ===TrickBot=== | ||
TrickBot is ransomware that was first identified in 2016. It is a trojan developed and operated by a group of hackers who initially made it as a banking trojan to steal financial data. TrickBot has become a highly modular, multi-stage suite of tools to conduct myriad illegal cyber activities.<ref>[https://us-cert.cisa.gov/sites/default/files/publications/TrickBot_Fact_Sheet_508.pdf CISA TrickBot Fact Sheet]</ref> TrickBot has been used | TrickBot is ransomware that was first identified in 2016. It is a trojan developed and operated by a group of hackers who initially made it as a banking trojan to steal financial data. TrickBot has become a highly modular, multi-stage suite of tools to conduct myriad illegal cyber activities.<ref>[https://us-cert.cisa.gov/sites/default/files/publications/TrickBot_Fact_Sheet_508.pdf CISA TrickBot Fact Sheet]</ref> TrickBot has been used | ||
* To exfiltrate data (email, credentials, point-of-sale info); | * To exfiltrate data (email, credentials, point-of-sale info); | ||
| Line 28: | Line 89: | ||
* Emotet and Bokbot | * Emotet and Bokbot | ||
*[[Spearphishing]], spam campaigns, [[malvertising]], and network vulnerabilities, such as Server Message Block, to gain initial access | *[[Spearphishing]], spam campaigns, [[malvertising]], and network vulnerabilities, such as Server Message Block, to gain initial access | ||
====Microsoft Disrupts Trickbot==== | |||
On October 12, 2020, [[Microsoft]] announced that it had disrupted Trickbot following a court order from the United States District Court for the Eastern District of Virginia, which granted Microsoft's request to halt Trickbot’s operations. Microsoft identified and disabled the infrastructure Trickbot used to communicate with and control victim computers, how infected computers talked with each other, and how Trickbot evaded detection and disruption previously. The corporation also identified the servers' IP addresses of servers.<ref>[https://blogs.microsoft.com/on-the-issues/2020/10/12/trickbot-ransomware-cyberthreat-us-elections/ New action to combat ransomware ahead of U.S. elections, Microsoft]</ref> | |||
===Netwalker=== | |||
In 2019, Netwalker was sent out into the world from the cybercrime group Circus Spider, who allowed hackers to rent access to their code in exchange for a percentage of the funds received.<ref>[https://www.varonis.com/blog/ransomware-statistics-2021/ 2021 Ransomware Stats, Varonis blog]</ref> | |||
===Conti=== | |||
Conti ransomware uses a double-extortion technique. Attackers send a [[phishing]] email originating from an address that the victim trusts.<ref>[https://www.varonis.com/blog/ransomware-statistics-2021/ 2021 Ransomware Stats, Varonis blog]</ref> | |||
===REvil=== | |||
Aka Sodin aka Sodinokibi, REvil has a reputation for extorting larger ransom payments than their competitors and promoting cybercrime forums.<ref>[https://www.varonis.com/blog/ransomware-statistics-2021/ 2021 Ransomware Stats, Varonis blog]</ref> | |||
The [[FBI]] accused REvil of orchestrating a ransomware attack on the world's largest meat processing company, JBS, in June 2021. JBS paid US$11 million in ransom to decrypt their files.<ref>[https://www.npr.org/2021/06/03/1002819883/revil-a-notorious-ransomware-gang-was-behind-jbs-cyberattack-the-fbi-says REvil behind JBS attack]</ref> | |||
====REvil Suddenly Goes Offline==== | |||
On July 13, 2021, Monitors discovered that a payment website and a blog run by the REvil group suddenly became unreachable, leading many to speculate that U.S. or Russian officials may be behind the disappearance.<ref>[https://www.bbc.com/news/technology-57826851 REvil: Ransomware gang websites disappear from the internet, BBC]</ref> | |||
===Ryuk=== | |||
From 2018 to 2020, Ryuk spread via malicious ([[phishing]]) emails with links and attachments, notoriously attacking EMCOR Group and Epiq Global. | |||
===SamSam=== | |||
From 2015 to 2018, SamSam infected the municipal/state services of Atlanta, Colorado, and San Diego and 200 public institutions/organizations.<ref>[https://gatefy.com/blog/real-and-famous-cases-ransomware-attacks/ Real and Famous Ransomware Cases, Gatefy]</ref> | |||
===CryptoLocker=== | |||
In 2013, a new type of ransomware, also known as Gameover Zeus, used the advent of Bitcoin transactions and the latest in encryption, using 2048-bit RSA key pairs generated from a command-and-control server. Only computers running a version of Windows are susceptible to Cryptolocker (it does not target Macs).<ref>[https://usa.kaspersky.com/resource-center/definitions/cryptolocker Cryptolocker, Kaspersky]</ref> | |||
===AIDS Trojan=== | |||
In 1989, one of the first ransomware attacks ever documented, also known as the PC Cyborg Virus, was released via floppy disk. Victims sent US$189 to a P.O. box in Panama to restore access to their systems.<ref>[https://www.crowdstrike.com/cybersecurity-101/ransomware/history-of-ransomware/ History of Ransomware, CrowdStrike]</ref> | |||
==References== | ==References== | ||
[[Category:DNS Abuse]] | |||
[[Category:Featured]] | |||
Latest revision as of 17:35, 30 March 2022
Ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. They threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid.
RaaS is a subscription for ransomware tools. RaaS allows cybercrime groups to extend their reach and decentralizes attacks, complicating efforts to disrupt them. The RaaS creators take a percentage of each successful ransom payment.[1]
Recent Statistics and History-Making Events
- Average downtime due to ransomware: 21 days[2]
- Average recovery time for organizations: 287 days[3]
- Total victims paid to decrypt their data: US$350 million[4]
- Change in payout from 2019 to 2020: 311% increase[5]
- Total victims paid to decrypt their data: US$350 million[6]
- Average individual payment: US$312,493[7]
- Year-over-year difference from 2019: 171% increase [8]
- Number of U.S.-based governments, healthcare facilities, and schools attacked: 2,400[9]
- The critical infrastructure sector that experienced more ransomware attacks than any other industry: Healthcare[10]
- On September 10, 2020, ransomware contributed to the first reported death related to a cyber attack, after an emergent patient had to be re-directed from a ransomware victim hospital in Germany.[11]
- On April 29, 2021, DHS Secretary Alejandro Mayorkas declared ransomware a national security threat.[12]
Mitigation
- CISA's StopRansomware.gov recommends that individual users:
- Update software and operating systems with the latest patches, because hackers most commonly attack outdated applications and operating systems;
- Never click on links or open attachments in unsolicited emails;
- Constantly back up data, keep it on a separate device, and store it offline;
- Use strong passwords; and
- Only connect to secure networks, use a VPN, and make sure you have a firewall.[13]
- Recommendations for organizations include:
- Heavily restrict user permissions to install and run software applications;
- Enable the strongest spam filters possible; and
- Configure firewalls to block access to known malicious IP Addresses.[14]
- On April 29, 2021, the Institute for Security and Technology launched the Ransomware Task Force (RTF), which released a comprehensive framework outlining 48 actions and their timelines for governments and industry leaders to undertake to disrupt the ransomware business model and mitigate attacks' impacts.[15]
- Alternatives to payment include:
- working with the No More Ransom Project, which helps victims decrypt data without paying attackers;
- working with law enforcement, such as the FBI, immediately after noticing the attack
- To manage the fallout, an industry has grown up around cyberattack recovery. Cyber insurance (aka cybersecurity insurance, cyber risk insurance, data breach insurance, or cyber liability insurance) protects against some of the financial and legal consequences of cyber risks and attacks. This industry is focused on mitigating the side effects of cyber attacks and data breaches.[16] The backstop support of insurance may encourage ransomware attackers, as insured victims may be more likely to pay.[17] However, insurance providers generally require that clients adhere to baseline security practices, connect victims to recovery experts and law enforcement, and leverage market tools to incentivize security standards and discourage organizations from paying ransom.[18]
- Zero Trust architecture limits lateral movement and contains the blast radius or ransomware attacks.[19]
Debates
To Pay or Not to Pay?
The "DON'T make it an option" Camp
- On June 10, 2021, FBI Director Christopher Wray testified before Congress that companies should not pay the ransom because doing so encourages more of this kind of activity and that victims may pay the ransom but not get their systems back.[20]
- U.S. Energy Secretary Jennifer Granholm supports legislation banning ransomware payments.[21]
- The Biden administration formed a multi-agency task force working on freeze ransomware payments made through cryptocurrency platforms[22]
- New York introduced and North Carolina passed bills to prohibit municipal ransomware payments.[23][24]
The "Maybe DO let it remain an option" Camp
- Bryan Hornung, the founder of cybersecurity firm Xact IT Solutions, argued that if companies cannot pay ransoms, they will have to close their doors and lawsuits will proliferate; also, the attackers may seek to extort individuals whose data are compromised if organizations do not pay.
- Ed Cabrera, CCO at Trend Micro, said that criminalizing ransom payments will lead hackers to make more lethal attacks and increase the pain.[25]
- In the Harvard Business Review, Rahul Telang opined that in attacking companies rather than consumers, ransomware is forcing organizations to pay a steep, direct price for lax security and ultimately focusing organizations' attention on improving their cybersecurity and protecting their networks.[26]
- Coveware's core business model is negotiating ransomware sums.[27]
Notorious Cases
Cobalt Strike
Cobalt Strike is the legitimate, commercially available tool used by network penetration testers that has been co-opted by threat actors.[28] It is also known as Agentemis, BEACON, and CobaltStrike, and the threat actors that have used it include APT 29, APT32, APT41, Anunak, Cobalt, Codoso, CopyKittens, DarkHydrus, FIN6, Leviathan, Mustang Panda, Shell Crew, Stone Panda, UNC1878, UNC2452, and Winnti Umbrella.[29]
Maze Cartel
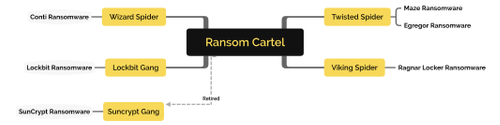
In June 2020, the Maze Cartel publically announced that TWISTED SPIDER, VIKING SPIDER, and LockBite were running a collaborative business arrangement.[30] In November 2020, Twisted Spider announced they were shutting down the cartel operations.[31]
The people who comprise the cartel originate from eastern Europe, primarily speak Russian, and ensure that their payloads do not execute on Russian victims. Twisted Spider used Maze ransomware from May 2019 to November 2020 and Egregor beginning in September 2020, each using its own malware, infrastructure, and online personas. The operators are very communicative with media, cybersecurity firms, and other cybercriminals.[32] Viking Spider began its ransom operations in December 2019. Wizard Spider has multiple teams and has been participating in attacks since 2016. The Lockbit Gang was the first to automate attacks. SunCrypt was the first gang to introduce denial of service attacks to extort victims.[33]
Darkside
Darkside is a group of hackers that carried out a significant ransomware attack in May 2021. In August 2020, Darkside introduced its Ransomware-as-a-Service (RaaS) in a press release. The group provides web chat support to victims, builds intricate data leak storage systems with redundancy, and performs financial analysis of victims prior to attacking. The group is suspected to be former IT security professionals and is known to have a code of conduct that includes not attacking hospitals, schools, non-profits, or governments, but rather big organizations. After the May 2021 Colonial Pipeline attack, Varonis’s reverse engineering revealed that Darkside’s malware checked device language settings to ensure that they don’t attack Russia-based organizations.[34] Darkside has Windows and Linux toolsets and is similar to NetWalker and REvil in that it has an affiliate program that offers anyone who helps spread their malware 10-25% of the payout.
Darkside
- runs command and control over TOR,
- avoids nodes where EDR is running,
- uses waiting periods,
- saves noisier actions for later stages,
- customizes code and connection hosts for each victim,
- obfuscates with encoding and dynamic library loading, and
- performs anti-forensics techniques, such as deleting log files.
TrickBot
TrickBot is ransomware that was first identified in 2016. It is a trojan developed and operated by a group of hackers who initially made it as a banking trojan to steal financial data. TrickBot has become a highly modular, multi-stage suite of tools to conduct myriad illegal cyber activities.[35] TrickBot has been used
- To exfiltrate data (email, credentials, point-of-sale info);
- For crypto-mining; and
- For host enumeration (reconnaissance of Unified Extensible Firmware Interface (UEFI) or Basic Input/Output System (BIOS) firmware)
Operators include:
Relies on:
- Emotet and Bokbot
- Spearphishing, spam campaigns, malvertising, and network vulnerabilities, such as Server Message Block, to gain initial access
Microsoft Disrupts Trickbot
On October 12, 2020, Microsoft announced that it had disrupted Trickbot following a court order from the United States District Court for the Eastern District of Virginia, which granted Microsoft's request to halt Trickbot’s operations. Microsoft identified and disabled the infrastructure Trickbot used to communicate with and control victim computers, how infected computers talked with each other, and how Trickbot evaded detection and disruption previously. The corporation also identified the servers' IP addresses of servers.[40]
Netwalker
In 2019, Netwalker was sent out into the world from the cybercrime group Circus Spider, who allowed hackers to rent access to their code in exchange for a percentage of the funds received.[41]
Conti
Conti ransomware uses a double-extortion technique. Attackers send a phishing email originating from an address that the victim trusts.[42]
REvil
Aka Sodin aka Sodinokibi, REvil has a reputation for extorting larger ransom payments than their competitors and promoting cybercrime forums.[43] The FBI accused REvil of orchestrating a ransomware attack on the world's largest meat processing company, JBS, in June 2021. JBS paid US$11 million in ransom to decrypt their files.[44]
REvil Suddenly Goes Offline
On July 13, 2021, Monitors discovered that a payment website and a blog run by the REvil group suddenly became unreachable, leading many to speculate that U.S. or Russian officials may be behind the disappearance.[45]
Ryuk
From 2018 to 2020, Ryuk spread via malicious (phishing) emails with links and attachments, notoriously attacking EMCOR Group and Epiq Global.
SamSam
From 2015 to 2018, SamSam infected the municipal/state services of Atlanta, Colorado, and San Diego and 200 public institutions/organizations.[46]
CryptoLocker
In 2013, a new type of ransomware, also known as Gameover Zeus, used the advent of Bitcoin transactions and the latest in encryption, using 2048-bit RSA key pairs generated from a command-and-control server. Only computers running a version of Windows are susceptible to Cryptolocker (it does not target Macs).[47]
AIDS Trojan
In 1989, one of the first ransomware attacks ever documented, also known as the PC Cyborg Virus, was released via floppy disk. Victims sent US$189 to a P.O. box in Panama to restore access to their systems.[48]
References
- ↑ Ransomware Stats 2021, Varonis blog
- ↑ Ransomware Payments Fall as Fewer Companies Pay Data Exfiltration Extortion Demands, Feb 1, 2021
- ↑ The State of Ransomware in the US: Report and Statistics 2020, Emisoft Blog, Jan 18, 2021
- ↑ 2021 Crypto Crime Report
- ↑ 2021 Crypto Crime Report
- ↑ 2021 Crypto Crime Report
- ↑ Ransomware Threat Assessments, Unit 42, Palo Alto Networks March 17, 2021
- ↑ Ransomware Threat Assessments, Unit 42, Palo Alto Networks March 17, 2021
- ↑ RTF Report 2021, pg. 7
- ↑ 2021 Cyber Security Stats, PurpleSec
- ↑ First Death from Ransomware, ZDNet
- ↑ Breaking Defense
- ↑ CISA Tips
- ↑ Ransomware FAQs, CISA
- ↑ RTF, IST
- ↑ Cyber insurance, Zeguro
- ↑ Extortion Economy, ProPublica
- ↑ RTF Report, IST, pg 13
- ↑ Adopting zero trust architecture can limit ransomware’s damage, VentureBeat
- ↑ FIB Director testifies, CSPAN
- ↑ Granholm on Meet the Press, NBC News
- ↑ White House Cybersecurity Task Force, CBS News
- ↑ 2019 NY Senate Bills
- ↑ 2021 NC Senate Bills
- ↑ Banning Ransomware payments could lead to new crises, Forbes
- ↑ Could Ransomware Attacks Ultimately Benefit Consumers? HBR, August 02, 2021
- ↑ Q2 Ransom Payments Decline, Coveware
- ↑ Cobalt Strike Usage Explodes Among Cybercrooks
- ↑ Cobalt Strike, Malpedia
- ↑ History of Ransomware, CrowdStrike
- ↑ https://chaslescorp.com/the-rise-and-fall-of-maze-cartel/ The rise and fall of Maze Cartel, ChaslesCorp]
- ↑ Ransom Mafia, Analyst1
- ↑ Ransom Mafia, Analyst1
- ↑ Analysis of Darkside, Varonis Blog
- ↑ CISA TrickBot Fact Sheet
- ↑ Wizard Spider, Crowdstrike
- ↑ WS sharing the same web, Crowdstrike
- ↑ WS Adversary, Crowdstrike
- ↑ Gold Blackburn, Secureworks
- ↑ New action to combat ransomware ahead of U.S. elections, Microsoft
- ↑ 2021 Ransomware Stats, Varonis blog
- ↑ 2021 Ransomware Stats, Varonis blog
- ↑ 2021 Ransomware Stats, Varonis blog
- ↑ REvil behind JBS attack
- ↑ REvil: Ransomware gang websites disappear from the internet, BBC
- ↑ Real and Famous Ransomware Cases, Gatefy
- ↑ Cryptolocker, Kaspersky
- ↑ History of Ransomware, CrowdStrike
